Hacking Enterprises – 2023 Red Edition
Sold out
Where
This is not the same address as the conference! Same building but different entrance.
Söder Mälarstrand 57
118 25 Stockholm
Day 1 (2023-09-12)
| 8.30 – 09.00 | Registration & breakfast |
| 9.00 – 12.00 | Training |
| 12.00 – 13.00 | Lunch |
| 13.00 – 15.00 | Training |
| 15.00 – 15.30 | Coffee break |
| 15.30 – 17.00 | Training |
Day 2 (2023-09-13)
| 8.30 – 09.00 | Registration & breakfast |
| 9.00 – 12.00 | Training |
| 12.00 – 13.00 | Lunch |
| 13.00 – 15.00 | Training |
| 15.00 – 15.30 | Coffee break |
| 15.30 – 17.00 | Training |
Updated for 2023, our Hacking Enterprises training is the natural counterpart to our popular Defending Enterprises course.
In this multi-layered offensive engagement, you will fully compromise a simulated enterprise in this immersive hands-on course that covers a multitude of TTP’s. Targeting modern operating systems including Windows 11, you’ll use modern techniques and focus on exploiting configuration weaknesses rather than throwing traditional exploits. Logical thinking and creativity will definitely be put to the test!
You will work to get initial access in a fictional organisation where multiple networks exist, some easily accessible, others not so. You’ll implant and establish C2, but manual techniques will always be emphasised so you’re equipped with the knowledge to work without reliance on frameworks.
Course content has been designed to reflect real-world challenges and you’ll perform numerous hands-on exercises including executing exploitative phishing campaigns against our simulated users for initial access, finding new networks that in turn bringing new challenges including IPv6 exploitation, subverting AMSI and AWL, passphrase cracking, pivoting, lateral movement, ADCS abuse, userland and privileged persistence via OOB channels and much more!
Course Contents
- Day 1
- MITRE ATT&CK framework
- Overview on using the in-LAB SIEM
- Offensive OSINT
- IPv6 discovery, enumeration and exploitation
- Pivoting, routing, tunnelling and SOCKS proxies
- Application enumeration and exploitation via pivots
- Linux living off the land and post exploitation
- C2 infrastructure and beacon deployment
- Exploitative phishing against our simulated enterprise users
- Living off the land tricks and techniques in Windows
- Day 2
- P@ssw0rd and p@ssphras3 cracking
- Windows exploitation and privilege escalation techniques
- Windows Defender/AMSI and UAC bypasses
- Situational awareness and domain reconnaissance
- RDP hijacking
- Bypassing AWL (AppLocker, PowerShell CLM and Group Policy)
- Extracting LAPS secrets
- Active Directory Certificate Services (AD CS) abuse
- Lateral movement for domain trust exploitation
- WMI Event Subscriptions for persistence
- Out of Band (OOB) data exfiltration
- Domain Fronting
Previous Knowledge
- A firm familiarity of Windows and Linux command line syntax
- Understanding of networking concepts
- Previous pentesting and/or SOC experience is advantageous, but not required
Student Requirements
- Students will need to bring a laptop to which they have administrative/root access, running either Windows, Linux or Mac operating systems
- Students will need to have access to VNC, RDP, SSH and OpenVPN clients on their laptop
Also Included
We realise that training courses are limited for time and therefore students are also provided with the following:
- 14-day extended LAB access after the course finishes
- 14-day access to a CTF platform with subnets/hosts not seen during training!
- Discord support channel access where our security consultants are available
Previous Training Locations
The 2023 version is currently taking registrations for Black Hat Asia and Black Hat USA. The 2022 version (and prior) training has been given at the following conferences.
- SEC-T Sweden (Physical – September 2022)
- Black Hat USA (Physical – August 2022)
- TROOPERS (VIRTUAL – October 2021)
- Black Hat USA (Virtual – August 2021)
- BruCON (Virtual – April 2021)
- TROOPERS (Virtual – March 2021)
- X33fcon (Virtual – March 2021)
- X33fcon (Virtual – November 2020)
- Black Hat Asia (Virtual – September 2020)
- Wild West Hackin’ Fest (Virtual – September 2020)
- Black Hat USA (Virtual – August 2020)
- BruCon Spring Training (Virtual – June 2020)
- Wild West Hackin’ Fest (Virtual – March 2020)
- 44CON (June 2019)
- Nolacon (May 2019)
- Wild West Hackin’ Fest (October 2019)
Training Platform
All students have access to a training platform (https://training.in.security) in which exercises are provided along with detailed instructions on how to achieve the task.
Figure 1: Landing page
Examples of the exercise structure/layout can be seen in Figure 2 overleaf.
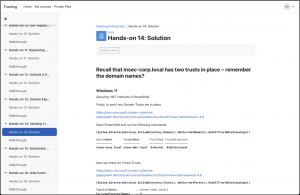
Figure 2: Exercise example
Twitter and Bio’s
Owen (@rebootuser) is a co-founder of In.security, a specialist cyber security consultancy offering technical and training services based in the UK. He has a strong background in networking and IT infrastructure, with well over a decade of experience in technical security roles. Owen has provided technical training to a variety of audiences at bespoke events as well as Black Hat, Wild West Hackin’ Fest, NolaCon, 44CON, TROOPERS, BruCON and Hack in Paris. He keeps projects at https://github.com/rebootuser.
Will (@Stealthsploit) co-founded In.security in 2018. Will’s been in infosec for over a decade and has helped secure many organisations through technical security services and training. Will’s delivered hacking courses globally at several conferences including Black Hat and has spoken at various conferences and events. Will also assists the UK government in various technical, educational and advisory capacities. Before Will was a security consultant he was an experienced digital forensics consultant and trainer.